Real-Time Monitoring Your Infrastructure
If your company wants to look for a security and policy strategy, Secure your business by identifying cyber threats & exploitable vulnerabilities before hackers are able to discover and exploit them.
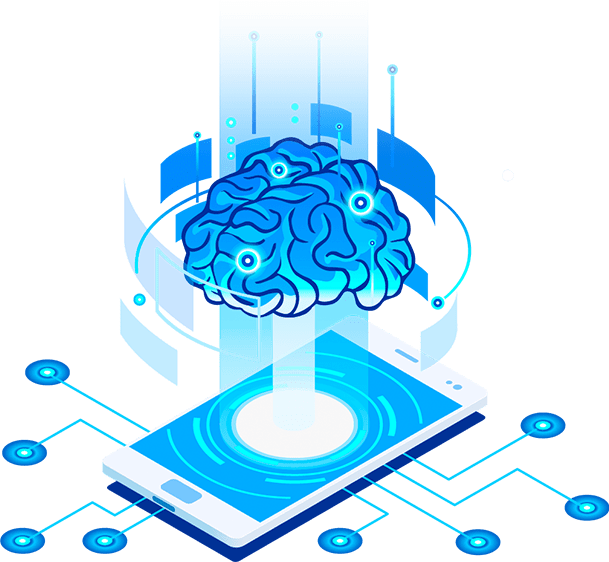
We follow strict quality assurance procedures to ensure highquality services. The quality of our services is bolstered by selfevident abilities with viable and demonstrated security assessment methodologies that are custom fitted for every condition sort



We are offer a full spectrum of security services that help you stay on top of security
aims to identify security issues resulting from insecure development practices in the design, coding and publishing of software or a website
The purpose of this test is to identify and exploit vulnerabilities in an application, and the way it interacts and transfers data with the backend systems.
aims to assess your network for vulnerabilities and security issues in servers, hosts, devices and network services
The process of auditing the source code for an application to verify that the proper security controls are present
a legal concern for organizations in many industries today. Regulatory standards like PCI DSS, ISO 27001 prescribe recommendations for protecting data and improving info security management in the enterprise
aims to investigate, analyze cybercrime in its several formats such as financial fraud, stalking, hacking, e-mail fraud, email spoofing, invoice fraud, email scams, banking scam, and virus infections